Monitor and regulate access to cloud applications
Skyhigh CASB through inline deployment modes (forward proxy and reverse proxy) enables real-time control over user access to approved and unapproved cloud services . No other CASB provider matches the comprehensive multi-mode coverage offered by Skyhigh Security.
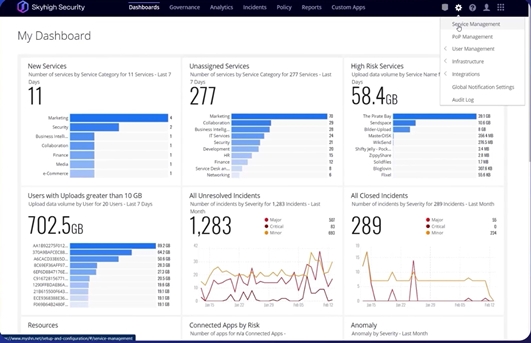
Control your data and operations in the cloud from any source
Gain control of your data across all cloud services and leverage the Skyhigh SSE framework to extend data protection to your web, network, and endpoints through policy enforcement unification and incident management.
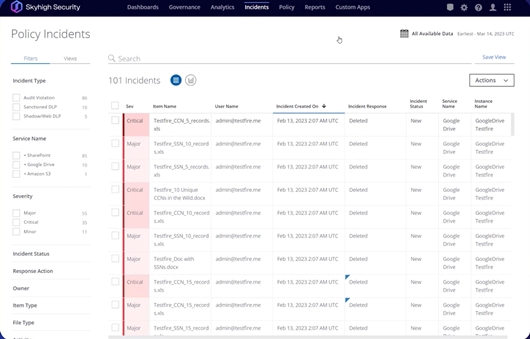
Protect against threats and cloud security misconfigurations
Analyze billions of cloud events using machine learning to detect and mitigate threats occurring across your cloud service portfolio. Reduce the risk of misconfiguration through continuous testing and automatic remediation of detected vulnerabilities. Skyhigh Security is the first CASB vendor to introduce MITER ATT&CK mapping into cross-cloud workflows
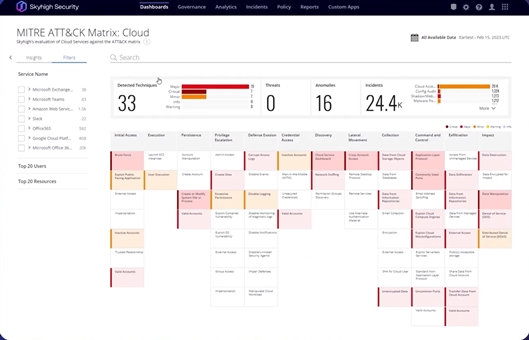
Gain visibility in cloud environments
Access a summary of the Shadow IT cloud services configured in your organization. Measure and improve your cloud environment against your competitors, review policy violation insights in your cloud environment, and implement recommendations to improve security maturity your secret. Cloud Security Advisor helps configure and fine-tune your Skyhigh CASB deployment.
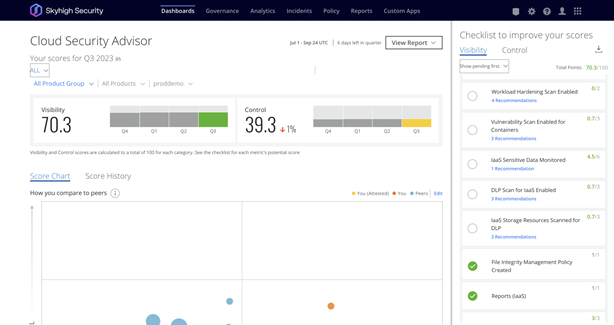
Most comprehensive API integration in the industry
Skyhigh CASB supports API integration for 40 applications













 Loading ...
Loading ...