THREAT HUNTING
Threat hunting is becoming increasingly important as businesses strive to overcome the latest cyber threats and swiftly respond to any potential attacks.

ACCESS
Suitable for
Assessment of hunting scope
Clearly define the scope of activities, set specific goals and timelines, and identify the necessary information to start the threat hunting process.

ACQUIRE
Suitable for
Search in the operating environment
Information sources such as system logs, event logs, network data and other resources are thoroughly exploited using many methods different, to find signals and signs of potential threats.

ANALYZE
Suitable for
Determine results and draw conclusions
Collected data and information are analyzed in depth, evaluated and results determined. If necessary, experts will conduct additional rounds of hunting, to draw the most accurate conclusions about the threat and related behaviors.

ACTION
Suitable for
Action, create new intelligence
Determine precautions and actions based on threat impact. At the same time, new intelligence (CTI) is created to provide support for future security operations.
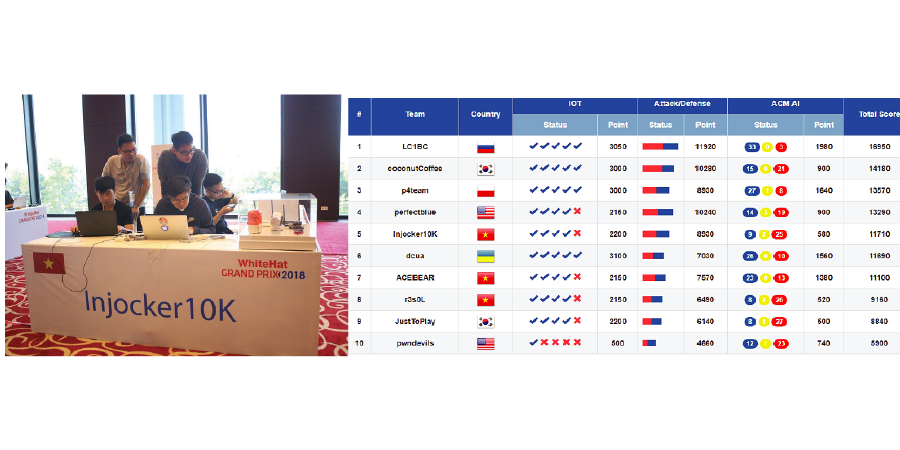
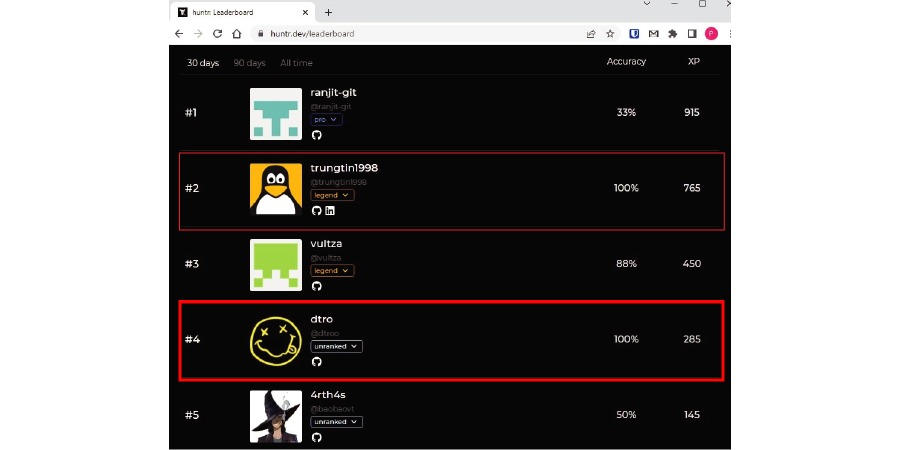
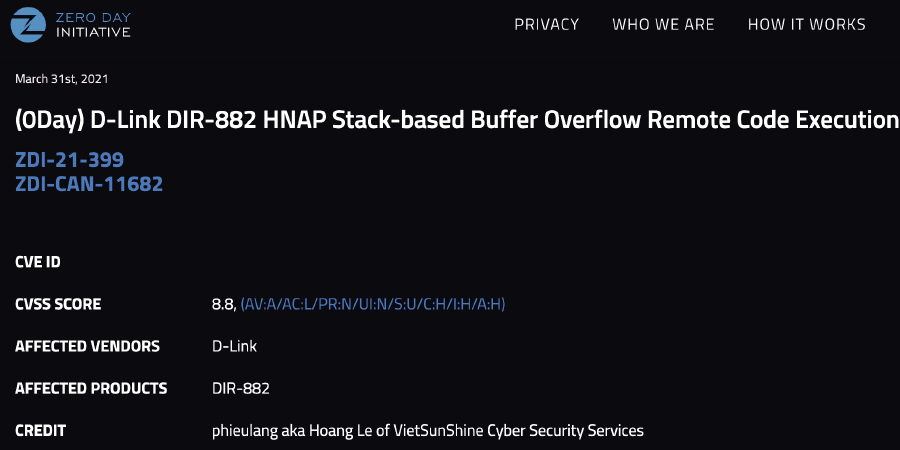
Awards and achievements
Data sources to examine
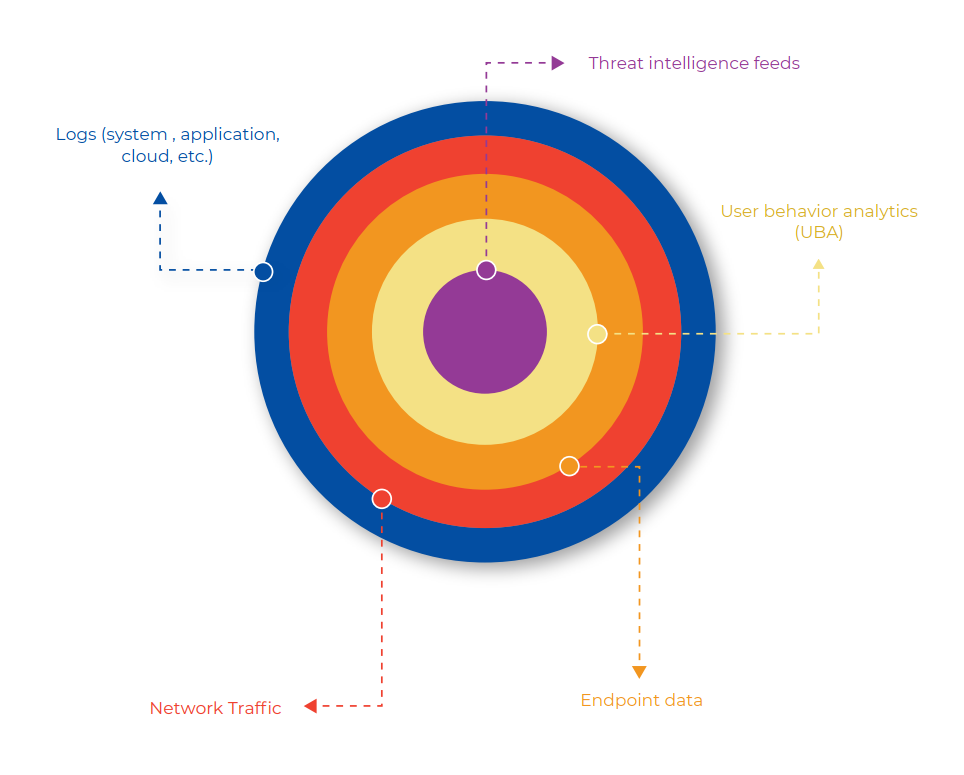
A4 Threat Hunting Framework provides a structure to
- Ensure progress is measurable
- Facilitate coordination
- Maximize utilization of analyst time
Vietsunshine experts will
- Hunt for both insider and outsider attacks
- Proactively hunt for known adversaries
- Search for hidden threats
- Strive to identify security threats before damage
- Mitigate without causing operational disruption
Leave contact
and we can advise you
We are happy to share advice and guide you with ideas about the service you need most











 Loading ...
Loading ...