DIGITAL INVESTIGATION AND INCIDENT RESPONSE
Investigation and Incident Response (DFIR) is a specialized service focused on identifying, mitigating, and investigating cybersecurity incidents. DFIR experts gather and analyze various pieces of information to determine who attacked, how they infiltrated, the precise steps the attacker took to compromise the system, and what measures can be taken to patch those security vulnerabilities.
What is digital forensics and incident response?
Digital Forensics and Incident Response (DFIR) is a field within cybersecurity that focuses on identifying, investigating, and remedying cyberattacks.
DFIR has two main components:
- Digital Forensics: A subset of forensic science that examines system data, user activities, and other digital evidence to determine whether a cyberattack is occurring and who may be behind it.
- Incident Response: The overall process that an organization follows to prepare for, detect, prevent, and recover from data breach incidents.

Benefits of Digital Investigation and Incident Response
- Responding to incidents quickly and accurately.
- Implementing consistent procedures when investigating and assessing incidents.
- Minimizing data loss or theft, as well as mitigating reputation damage caused by cybersecurity attacks.
- Strengthening existing security protocols and procedures through a deeper understanding of threat context and current risks.
- Faster recovery from security events and limiting disruptions to business operations.
- Supporting the prosecution of threat actors through evidence and documentation.

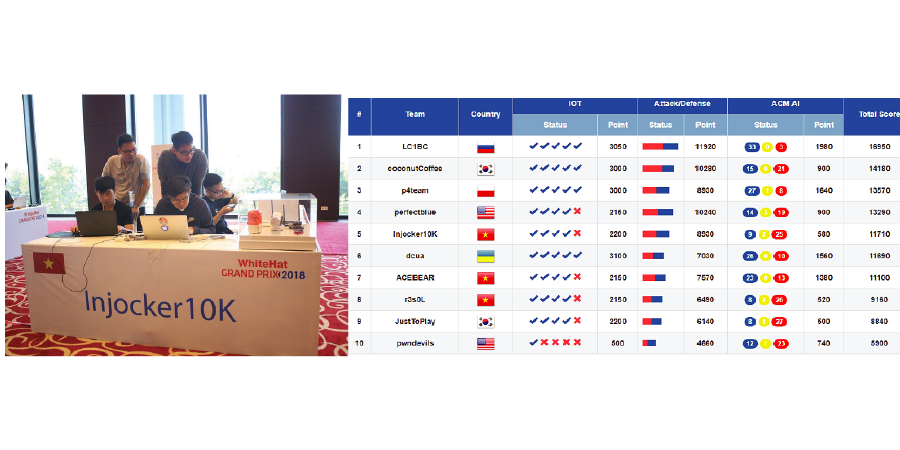
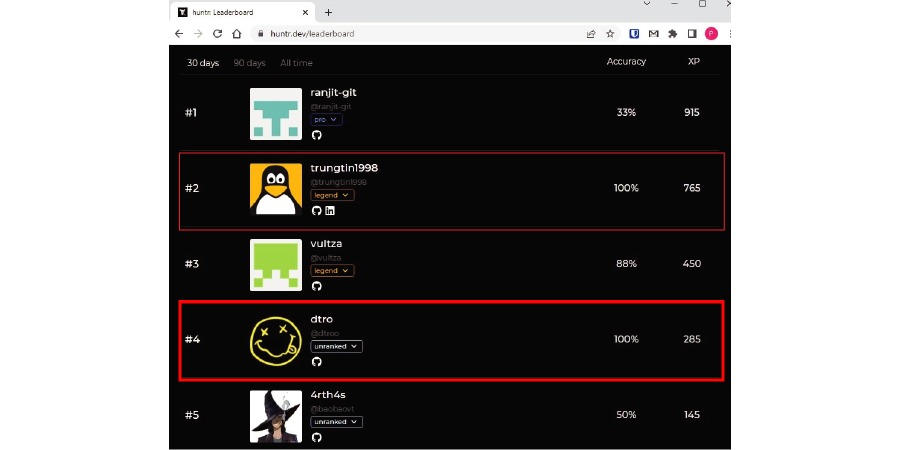
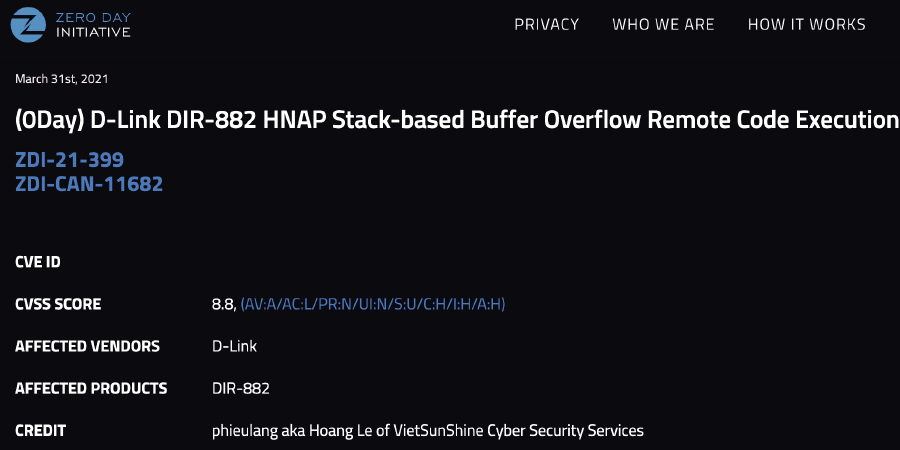
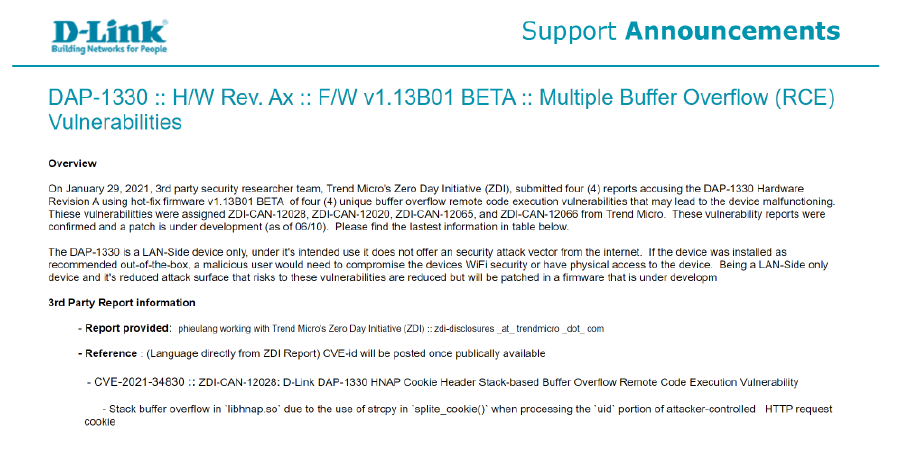
Awards and achievements
Implementation content
1. Reception
- Receive information from partners regarding the timing of the attack, consequences, and current status of the system.
- Identify the situation: whether the system has been attacked, is currently under attack, or has been altered following the restoration process.
- Scope of the incident: system-wide network, individual computer, data breach.
2. Classification
- Deception attacks.
- Malicious code and data encryption attacks.
- Attacks aimed at sabotage.
- Other forms of attacks.
3. Evidence Collection
- Information about contact points.
- Network diagram of the system.
- Affected targets (server type, software, network equipment, operating system...).
- Access accounts to affected systems for data extraction and analysis.
- System log information (Logs).
- Memory and network connection status.
- Tampered data samples.
- Malicious code samples.
4. Analysis
- Analysis of vulnerabilities in servers, network devices, and software within the system.
- Analysis of log samples.
- Timeline recording of events occurring within the system before, during, and after the incident.
- Malicious code analysis.
5. Reporting
- Summarize investigation results, fully document digital evidence, identify causes, and report on the outcome of the resolution.
- Propose solutions to improve cybersecurity for the system, including procedures, hardware, and software.
Leave contact
and we can advise you
We are happy to share advice and guide you with ideas about the service you need most











 Loading ...
Loading ...