V-SOC
VietSunshine delivers comprehensive SOC services, enabling your organization to reduce pressure free up time to engage in other projects aimed at achieving broader organizational goals.

TIER 1: ALERT ANALYST
Suitable for
- Monitor and operate MS Sentinel SIEM systems as per client requirements (24/7).
- Record, log, and process incidents using ticketing systems.
- Coordinate with relevant stakeholders of clients during incidents.
- Generate reports related to incident handling procedures.
- Document and respond to customer inquiries.
- Record customer requests.
- Adhere to internal SOC processes and comply with ISO 27001 and ISO 22301 security standards.

Tier 2: Incident Response
Suitable for
- Receive requests and tickets from monitoring/operations/customer teams.
- Respond to incidents according to procedures and comply with SLA timelines agreed with customers.
- Provide on-site support at customer systems.
- Prepare reports related to incident handling processes and system recovery procedures.
- Assist customers in system recovery efforts.
- Report and present to customers the outcomes of issue resolution within tickets.

Tier 3: Expert Security Analyst
Suitable for
- Receive requests from incident response team and monitoring/operations team (from Tier 1 & 2).
- Responsible for investigating, analyzing, and conducting in-depth research into serious incidents.
- Conduct malware analysis, reverse engineering, security vulnerability analysis, payloads, exploit code analysis, etc.
- Monitor global cybersecurity landscape, APT organizations, newly disclosed vulnerabilities, new malware strains. This includes resources like Mandiant Advantage, IBM, and other public sources.
- Present to customers the findings from in-depth investigations and incident analysis.

Tier 4: SOC Manager
Suitable for
- Oversee overall operations of the SOC team.
- Develop and present incident response plans for customers.
- Prepare compliance reports and support audit processes.
- Present findings and incident response plans to customers.
- Manage documentation and compile regular reports for customers.
Challenges of businesses/organizations
In the current landscape where threats are evolving rapidly, businesses need to prioritize cybersecurity efforts to shield themselves from potential cyberattacks. The lack of internal manpower, expertise, and knowledge about emerging threats pose significant challenges for businesses and organizations.

What is information security monitoring service?
Information security monitoring service is a comprehensive 24x7 service designed to monitor the security of clients' IT systems. It provides alerts on risks, investigates, and responds to IT system threats, and offers specific recommendations to enhance the security of the organization/business.

Benefits of using VietSunshine's information security monitoring service (V-SOC)
With a team of over 20 highly experienced experts and partnerships with leading technology vendors worldwide, V-SOC brings several benefits to customers:
- Expertise and security insights.
- 24/7 threat monitoring and detection.
- Cost-effective investment.
- Proactive threat hunting.
- Automated compliance.
- Vulnerability and risk assessments.

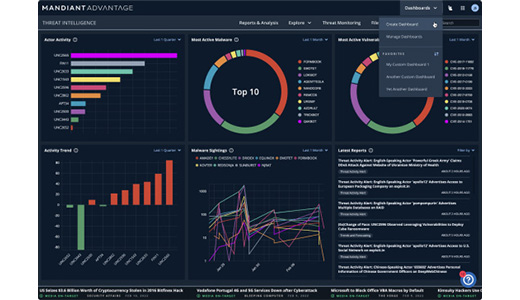
Technology platform_Mandiant (Google Cloud)
"Mandiant’s strength in threat intelligence is in large part due to the reputation and visibility provided via the company’s robust incident response consultancy, security controls business, and managed security services. The visibility gained from those supporting services is ahead of the pack" - Forrester
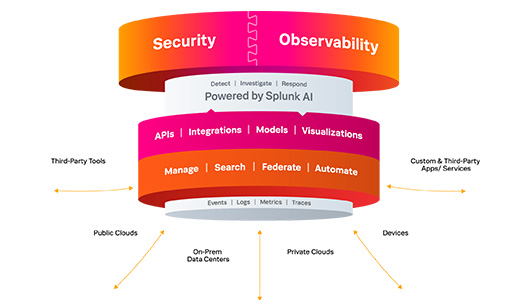
Technology platform_Splunk
Protect your business and elevate your security operations with a best-in-class data platform, advanced analytics and automated investigations and response.
- 80% reduction in alert volume
- 30 secs to complete processes that once took 30 minutes
- 2x improvement in alert fidelity
Technology platform_Trellix
Reduce the time to detect and respond to cyber attacks with the most open and comprehensive AI-powered XDR platform. Strengthen your security posture and protect your organization with confidence.
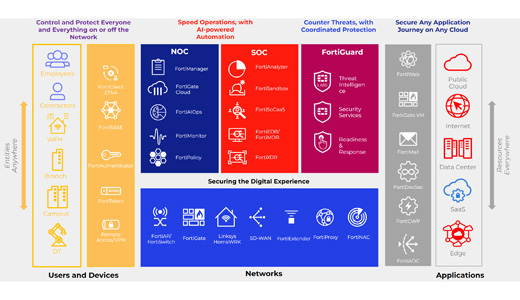
Technology platform_Fortinet
Fortinet Security Fabric brings together the concepts of convergence and unification to deliver comprehensive cybersecurity protection for all users, devices, and applications, and across all network edges.
Technology platform_OPSWAT
OPSWAT's platform supports IT and OT environments with cloud, software and hardware solutions integrated by design.
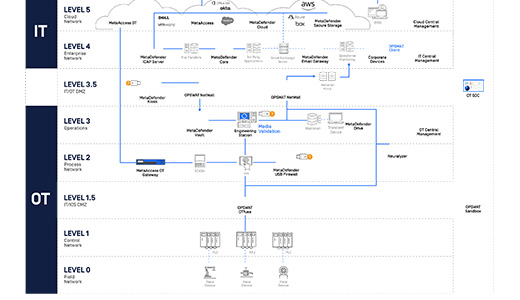
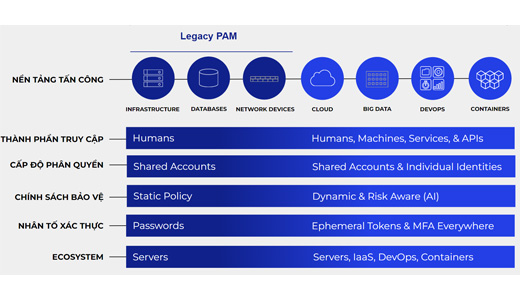
Technology platform_Delinea
PAM is a privileged account management solution, allowing identification and authorization of users with access rights to servers, databases, and network devices corresponding to an account in the server such as Administrator, or 1 regular accounts have limited rights, depending on the policy you have specified on PAM.
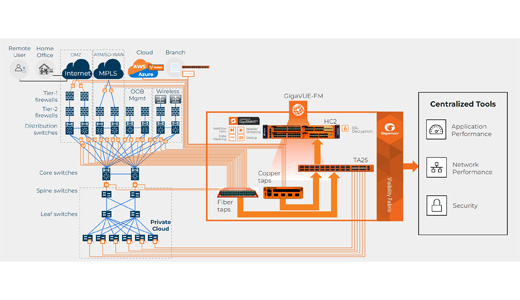
Technology platform_Gigamon
Deep visibility helps IT organizations proactively mitigate risk, deliver superior user experiences, and reduce cost and complexity in cloud management.
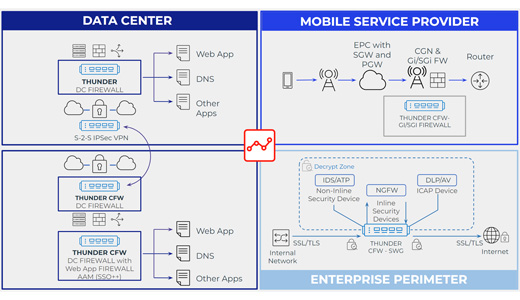
Technology platform_A10 Networks
A10 Networks' cloud-based and on-premises security solutions protect your applications and infrastructure from cyberattacks, including multi-vector and malware DDoS attacks. malware in encrypted traffic.
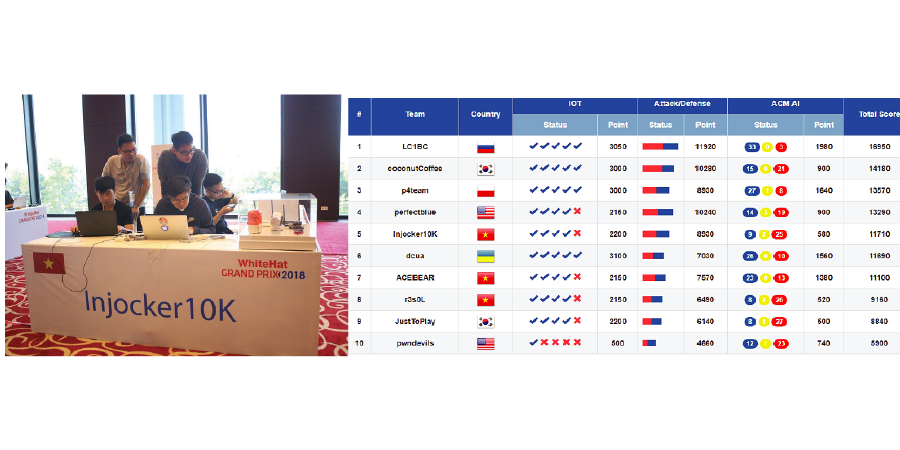
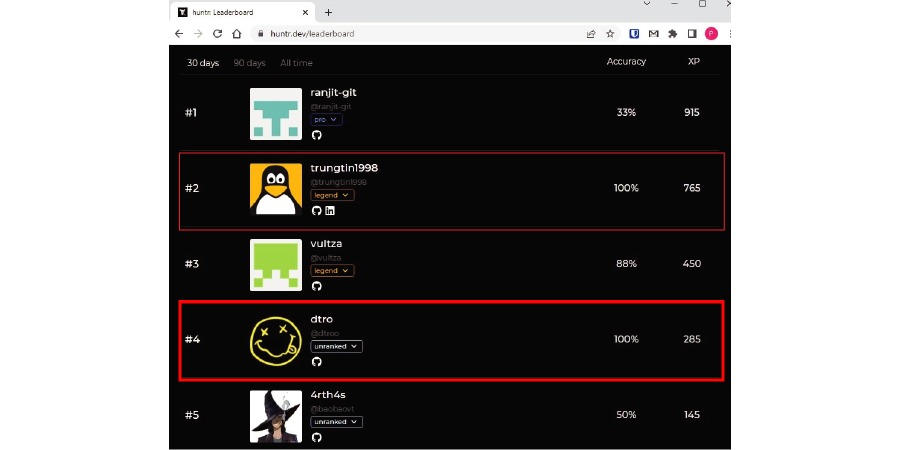
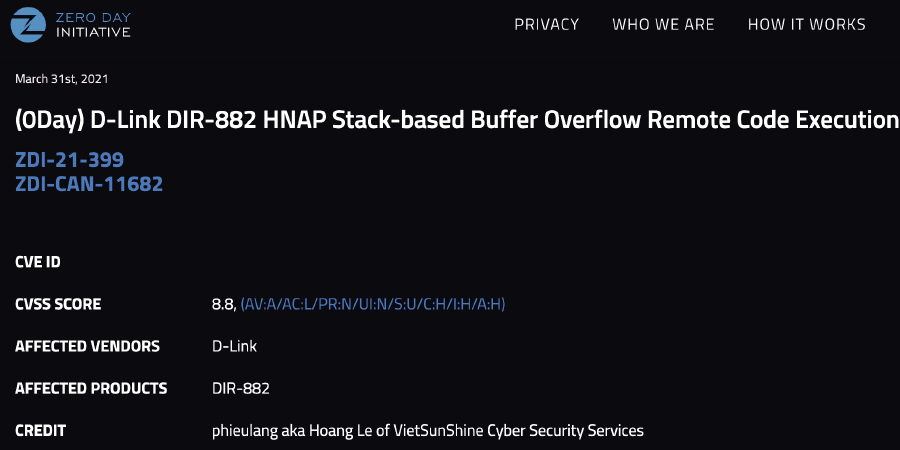
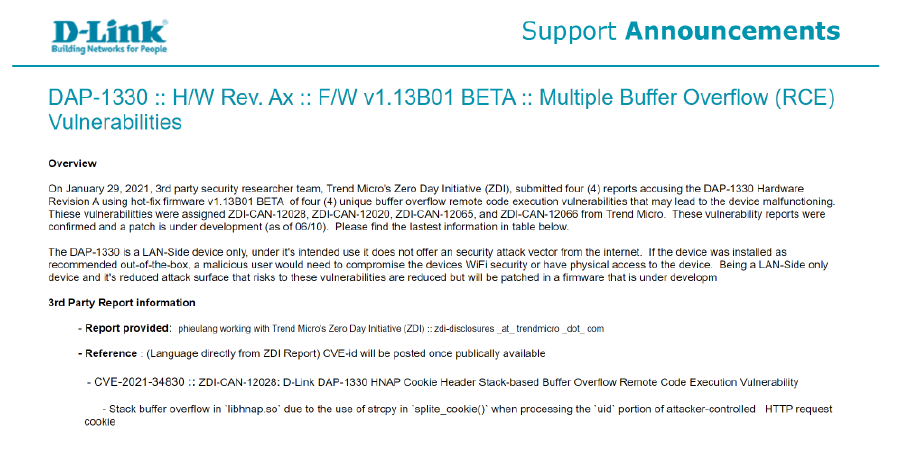
Awards and achievements
V-SOC
TECHNOLOGY

PEOPLE

PROCESS

Leave contact
and we can advise you
We are happy to share advice and guide you with ideas about the service you need most











 Loading ...
Loading ...