Ensure security and compliance across your hybrid cloud
Today, 90% of organizations operate in a hybrid and multi-cloud world. Moving to a multi-cloud strategy helps organizations accelerate their digital transformation efforts, but also creates new challenges around security, consistent digital experiences, and operating costs.< /p>
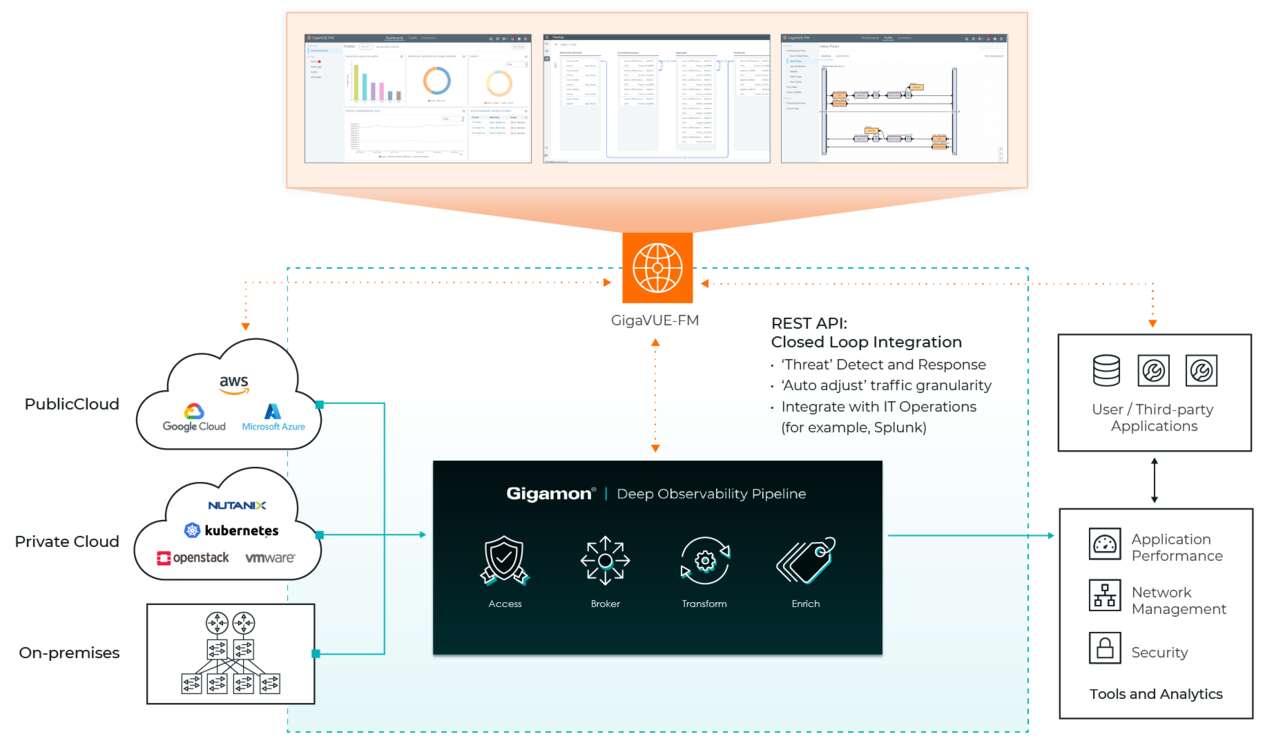
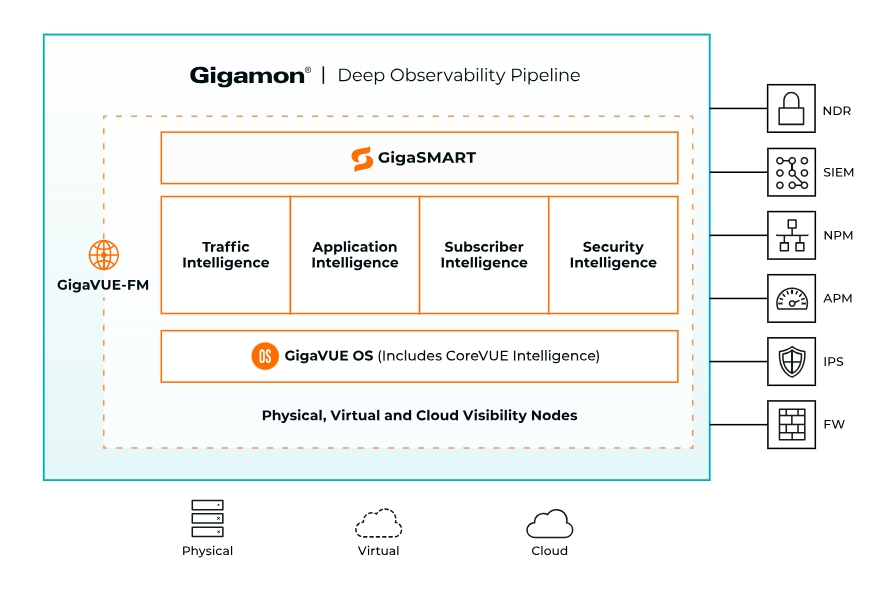
Gigamon Deep Observability Pipeline is based on the GigaVUE Cloud Suite™, amplifying the power of your cloud, security, and observability tools with network-native intelligence and insights to eliminate eliminate security and performance blind spots so you can:
- Proactively minimize security and compliance risks
- Delivering a superior digital experience
- Reduce cost and complexity across hybrid environments
Gigamon enables you to achieve the flexibility and resiliency benefits of hybrid and multi-cloud infrastructure, while reducing the risks and costs of security and compliance administration.
Next Level Observability
Deep observability defines a new frontier – complement your security and observability tools with the actionable network-level intelligence you need to ensure compliant governance and security, speed up root cause analysis of performance bottlenecks, and reduce operational costs associated with managing your hybrid and multi-system cloud IT infrastructure clouds.

Complete solution to accelerate your cloud adoption
Gigamon Deep Observability Pipeline goes beyond current observability approaches that rely solely on metrics, event, log, and trace (MELT) logging. According to IDC, network-native intelligence and insight provide an immutable source of information that contributes strong value to security situations and practices when used in conjunction with log-based tools. sign.
Gigamon expands the value of cloud, security tools and your visibility with real-time network intelligence pulled from packets, flows, and application metadata to provide complete performance management and in-depth protection across IT infrastructure your hybrid and multi-cloud.
This enables you to move into a proactive security posture by identifying threats and anomalies to minimize risk exposure and accelerate incident handling.












 Loading ...
Loading ...