Expose hidden threats and build business resilience.
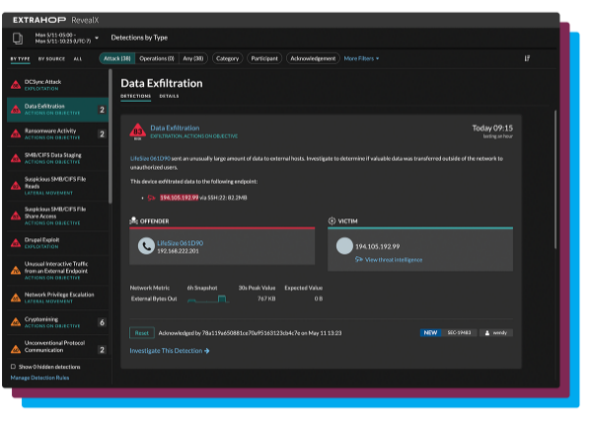
Network detection and response (NDR) is an emerging category of cybersecurity solution that ingests and analyzes network traffic to detect suspicious activity and understand security risks and exposure. NDR combines machine learning-powered detections, behavioral analysis, and signature-based detections for known IOCs. Best-in-class NDR solutions also use decryption and protocol decoding to uncover threats hiding in encrypted traffic. Streamlined workflows enable cybersecurity teams to quickly investigate down to packet-level context and respond with confidence.
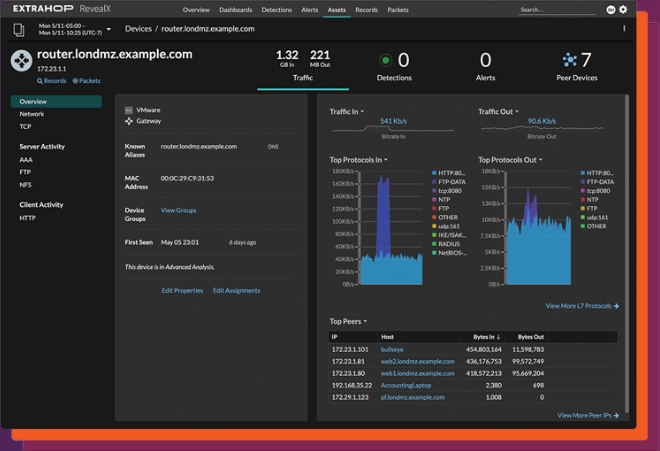
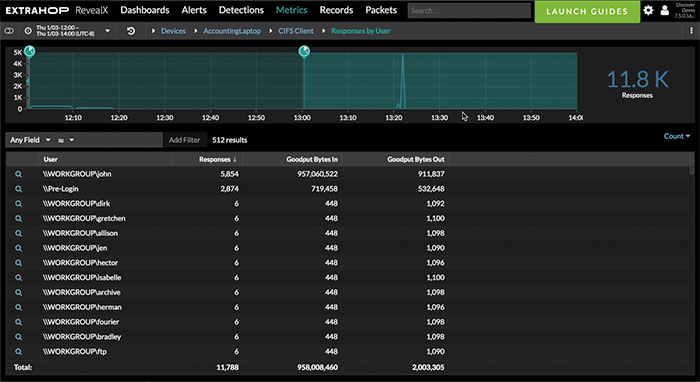
Reclaim the advantage over cyber attackers with complete network visibility that fills coverage gaps left by EDR, SIEM, and logs. With agentless RevealX NDR, security teams have the network intelligence they need to investigate smarter, stop threats faster, and move at the speed of risk.
Integrations and automations
Integrate with CrowdStrike, Splunk, Netskope, and more to enhance your cybersecurity with complete network visibility, real-time detection, and streamlined investigations.












 Loading ...
Loading ...